What is VAPT?
VAPT stands for Vulnerability Assessment and Penetration Testing. Vulnerability Assessment looks at your digital assets (e.g. applications, devices, network) to identify weaknesses and indicate potential security vulnerabilities. Vulnerability Assessment and Penetration Testing (VAPT Testing) are a method of detecting security gaps in a network or software. A Penetration Test is a process in which testing borders on maliciously exploited vulnerabilities in a system and Tesla alerts an organization.
Why do organizations need VAPT?
Every aspect of IT Infrastructure (Applications, Network devices & Cloud Infrastructure) will have vulnerabilities irrespective of an organization’s size. The belief that cybercriminals typically bypass small and medium-sized enterprises is misleading, as small companies generally have weak security and can easily be exploited by attackers. Seventy-seven percent of cybercriminals target small companies primarily due to lack of security. In fact, 93 percent of small and medium businesses (SMEs) became involved in a cyberattack which they classified as a significant problem. They indicated that their operations were impeded, nearly all their finances and savings were reported as lost. A total of 93 percent reported some damage with 31 percent reporting reputational damage, loss of clients, and difficulty in bringing in new clients due to reputational damage, as well as difficulty in retaining or hiring new employees or coming up with new business.
VAPT is an important aspect of securing your organization by identifying security vulnerabilities and providing suggestions for remedial actions in advance.
Benefits of VAPT
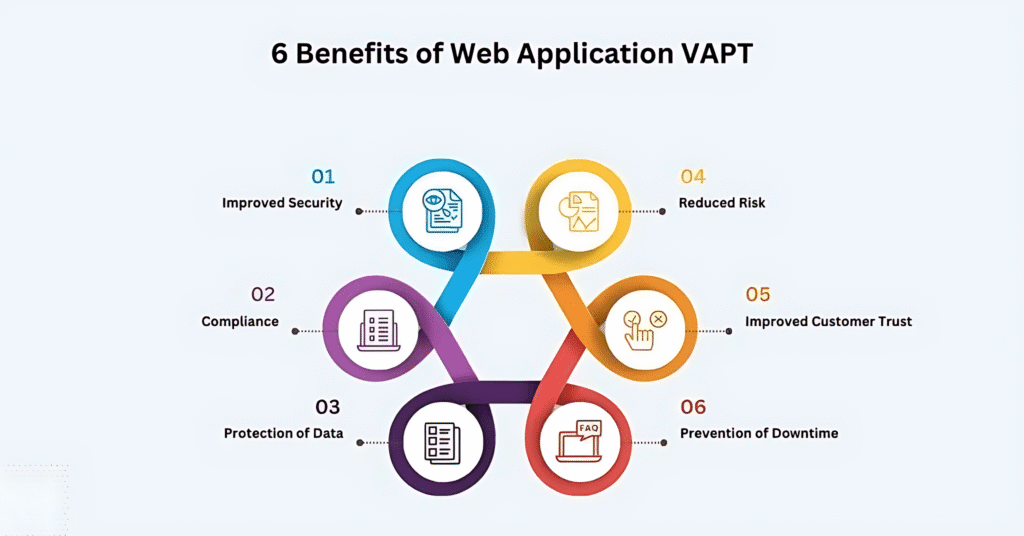
- Protects confidential data and information from unauthorized access/theft or unauthorized data breaches.
- Provides a structured method of identifying major vulnerabilities, which enhances risk management.
- VAPT Testing provides a comprehensive evaluation and analysis of web/mobile applications and network infrastructure.
- Identifies holes and flaws in the infrastructure that lead to cyber-attacks.
- Enhances the credibility of the organization by having a secure data network.
- Protects businesses from revenue loss and reputational damage.
- Helps to achieve and maintain compliance with national standards.
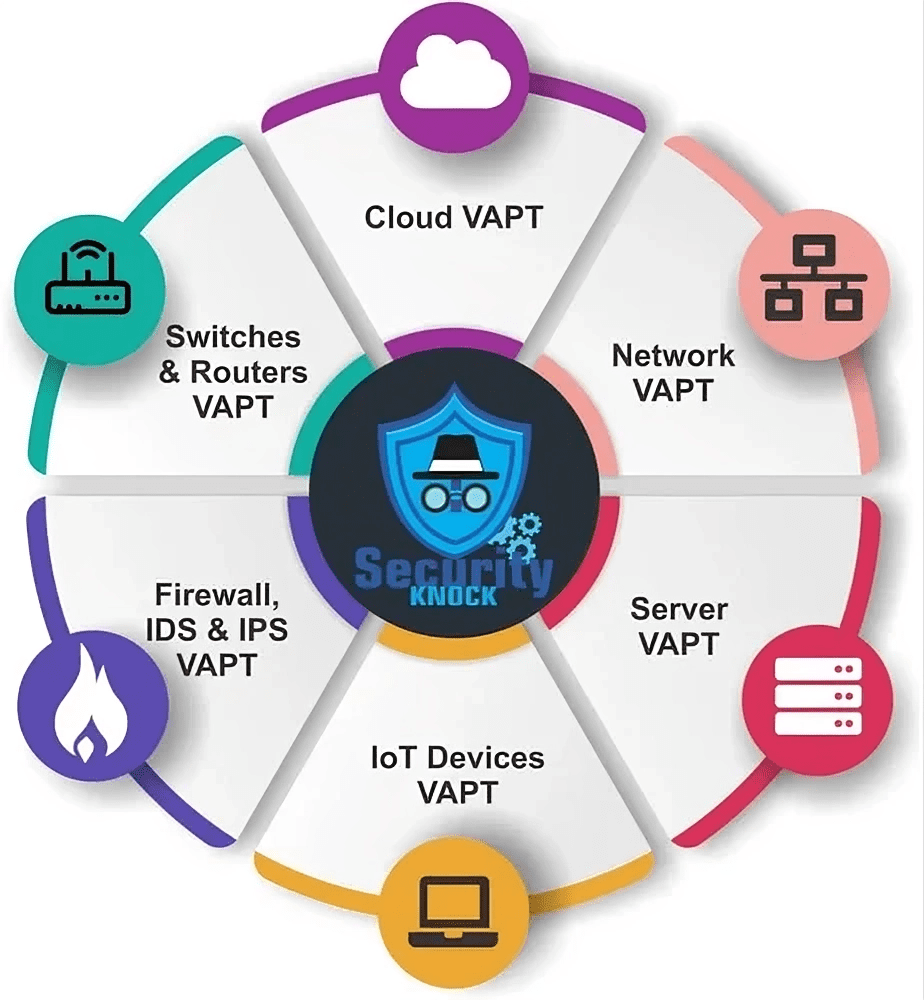
VAPT Services

Web Application VAPT

MOBILE APPLICATION VAPT

NETWORK PENETRATION VAPT

SERVER PENETRATION VAPT

CLOUD PENETRATION VAPT

SWITCHES & ROUTER VAPT

FIREWALL,IDS & IPS VAPT

IOT DEVICES VAPT
How can we help you?








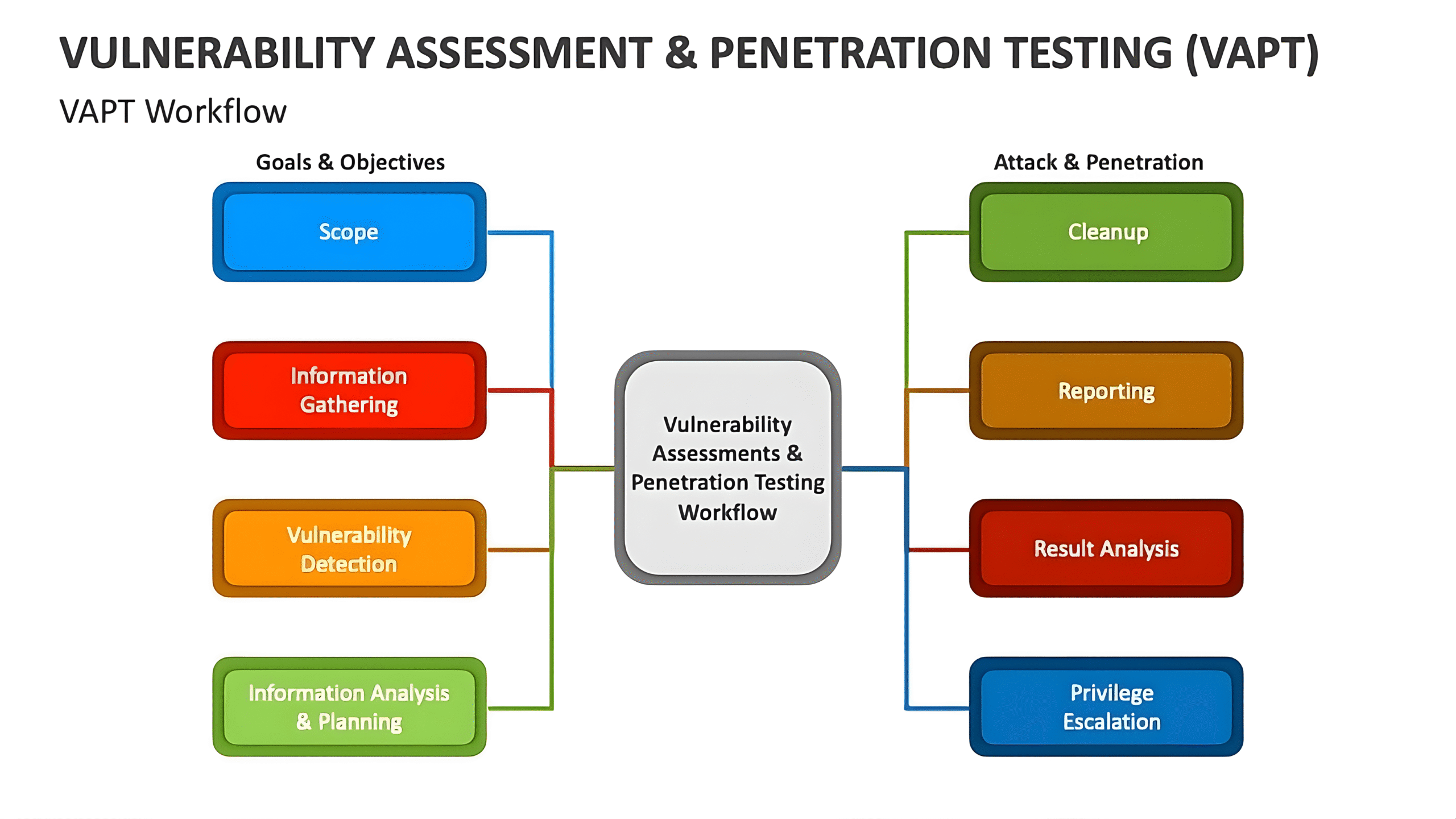
What you will get ?
Assessment Report
Remediation Guideline
Controls Implementation Assistance
Secure Network & Application Environment
Meeting Compliance & Regulation Requirement
Insight of Developing the IT Security Roadmap
