1 . Executive Summary:
Our team conducted a comprehensive penetration test across 40 servers for [Client Name Masked], simulating real-world cyberattacks. The assessment aimed to evaluate the resilience of the network infrastructure and detect vulnerabilities that could lead to unauthorized access, data theft, or service disruption.
One with the goals of:
– Identifying if a remote attacker could penetrate {Masked} defenses.
– Determining the impact of a security breach.
Efforts were placed on the identification and exploitation of security weaknesses that could allow a remote attacker to gain unauthorized access to organizational data. The attacks were conducted with the level of access that a general employee would have. Overall, Our team was able to achieve the goals of the assessment and exfiltrate the targeted data.
The key strong points of application are
– Immediate response on crashed servers
– Immediate restore when data is lost
The Key weaknesses are
– Permissions are not set to shares.
– Lower version operating systems
– Access controls are not enforced in few areas.
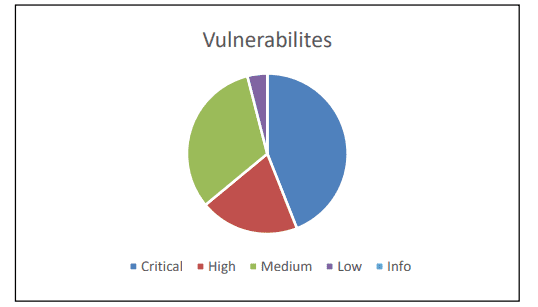
- Total number of findings: 25
- Total number of critical findings: 11
- Total number of high findings: 5
- Total number of moderate findings: 8
- Total number of low findings: 1
- Total number of informational findings: 0
2 . Findings
Critical Risk Findings
- Shellshock vulnerability
- Privilege Escalation via Dirty Cow
- NFS Exported Share Information Disclosure
- Vertical Privilege escalation to view admin pages as a user
- MongoDB Service Without Authentication
High Risk Findings
- NFS Exported Share Information Disclosure
- OpManager default credentials
- Sonarcube default password
- SIEM password from leaked DB
Moderate Risk Findings
- NFS Shares World Readable
- Unix Operating System Unsupported Version Detection
- Postgres sql DB Weak credentials
- Gsoap 2.7 vulnerability
- Microsoft SQL Server Unsupported Version Detection
- Microsoft Windows SMB Shares Unprivileged Access
- MS KB2269637: Insecure Library Loading Could Allow Remote Code Execution
- Windows vulnerable packages
Low Risk Findings
- Phpinfo() Information disclosure
Critical Risk Findings
Shellshock vulnerability
Shellshock, also known as Bashdoor is a family of security bugs in the widely used Unix Bash shell, the first of which was disclosed on 24 September 2014. Many Internet-facing services, such as some web server deployments, use Bash to process certain requests, allowing an attacker to cause vulnerable versions of Bash to execute arbitrary commands. This can allow an attacker to gain unauthorized access to a computer system.
Severity: Critical
Remediation:
The following is recommended to prevent Shellshock vulnerability
– apt-get update && apt-get -u dist-upgrade.
Privilege Escalation via DirtyCow
Dirty COW (Dirty copy-on-write) is a computer security vulnerability for the Linux kernel that affects all Linux-based operating systems including Android. It is a local privilege escalation bug that exploits a race condition in the implementation of the copy-on-write mechanism in the kernel’s memory-management subsystem. The vulnerability was discovered by Phil Oester. Because of the race condition, with the right timing, a local attacker can exploit the copy-on-write mechanism to turn a read-only mapping of a file into a writable mapping. Although it is a local privilege escalation, remote attackers can use it in conjunction with other exploits that allow remote execution of non-privileged code to achieve remote root access on a computer. The attack itself does not leave traces in the system log.
Severity: Critical
Remediation:
The following is recommended to prevent Privilege Escalation via DirtyCow apt-get update && apt-get – u dist-upgrade
NFS Exported Share Information Disclosure
Mountable NFS Shares is a high risk vulnerability that is one of the most frequently found on networks around the world. This issue has been around since at least but has proven either difficult to detect, difficult to resolve or prone to being overlooked entirely.
Severity: Critical
Remediation:
Configure NFS on the remote host so that only authorized hosts can mount its remote shares and never configure the NFS share to Root Path (/var/www/html) because an attacker can put backdoor in php and comprimise the whole system.
Vertical Privilege escalation to view admin pages as a user
Mountable NFS Shares is a high risk vulnerability that is one of the most frequently found on networks around the world. This issue has been around since at least but has proven either difficult to detect, difficult to resolve or prone to being overlooked entirely.
Severity: Critical
Remediation:
Configure NFS on the remote host so that only authorized hosts can mount its remote shares and neverconfigure the NFS share to Root Path (/var/www/html) because an attacker can put backdoor in php and comprimise the whole system.
MongoDB Service Without Authentication
MongoDB, a document-oriented database system, is listening on the remote port, and it is configured to allow connections without any authentication. A remote attacker can therefore connect to the database system in order to create, read, update, and delete documents, collections, and databases.
Severity: Critical
Remediation:
Authentication should enabled in mongodb
High Risk Findings
NFS Exported Share Information Disclosure
Mountable NFS Shares is a high risk vulnerability that is one of the most frequently found on networks around the world. This issue has been around since at least but has proven either difficult to detect, difficult to resolve or prone to being overlooked entirely.
Severity: High Risk
Remediation:
Configure NFS on the remote host so that only authorized hosts can mount its remote shares and never configure the NFS share to Root Path (/var/www/html) because an attacker can put backdoor in php and comprimise the whole system.
OpManager default credentials
OpManager default credentials. The defualt credentials are admin & admin.
Severity: High
Remediation:
Password should be changed.
Sonarcube default password
SonarCuber default password found. The username and password is admin.
Severity: High
Remediation:
The default credentials should be changed.
SIEM password from leaked DB
The nagios server username & password are weak. The username and password is nagiosadmin & eNoah123. This was from the leaked mysql DB in a Ubuntu server.
Severity: High
Remediation:
Password should be changed.
Moderate Risk Findings
NFS Shares World Readable
ountable NFS Shares is a high risk vulnerability that is one of the most frequently found on networks around the world. This issue has been around since at least but has proven either difficult to detect, difficult to resolve or prone to being overlooked entirely.
Severity: Moderate
Remediation:
Place the appropriate restrictions on all NFS shares
Unix Operating System Unsupported Version Detection
According to its self-reported version number, the Unix operating system running on the remote host is no longer supported.Lack of support implies that no new security patches for the product will be released by the vendor. As a result, it is likely to contain security vulnerabilities.
Severity: Moderate
Remediation:
Upgrade to a version of the Unix operating system that is currently supported (eg 17.10)
Postgres sql DB Weak credentials
PostgreSQL was having weak credentials, which were easy to brute-force.
Severity: Moderate
Remediation:
Use strong passwords.
Gsoap 2.7 vulnerability
Integer overflow in the soap_get function in Genivia gSOAP 2.7.x and 2.8.x before 2.8.48, as used on Axis cameras and other devices, allows remote attackers to execute arbitrary code.
Severity: Moderate
Remediation:
Upgrade to the new version
Microsoft SQL Server Unsupported Version Detection
According to its self-reported version number, the installation of Microsoft SQL Server on the remote host is no longer supported. Lack of support implies that no new security patches for the product will be released by the vendor. As a result, it is likely to contain security vulnerabilities.
Severity: Moderate
Remediation:
Upgrade to a version of the Unix operating system that is currently supported
Microsoft Windows SMB Shares Unprivileged Access
The remote has one or more Windows shares that can be accessed through the network with the given credentials. Depending on the share rights, it may allow an attacker to read/write confidential data.
Severity: Moderate
Remediation:
To restrict access under Windows, open Explorer, do a right click on each share, go to the ‘sharing’ tab,
and click on ‘permissions’
Insecure Library Loading Could Allow Remote Code Execution
The remote host is missing Microsoft KB2264107 or an associated registry change, which provides a
mechanism for mitigating binary planting or DLL preloading attacks.
Insecurely implemented applications look in their current working directory when resolving DLL
dependencies. If a malicious DLL with the same name as a required DLL is located in the application’s current
working directory, the malicious DLL will be loaded.A remote attacker could exploit this issue by tricking a user into accessing a vulnerable application via a
network share or WebDAV folder where a malicious DLL resides, resulting in arbitrary code execution.
Severity: Moderate
Remediation:
Microsoft has released a set of patches for Windows XP, 2003, Vista, 2008, 7, and 2008 R2 :Please note
this update provides a method of mitigating a class of vulnerabilities rather than fixing any specific
vulnerabilities.
Additionally, these patches must be used in conjunction with the ‘CWDIllegalInDllSearch’ registry setting
to have any effect. These protections could be applied in a way that breaks functionality in existing applications.
Refer to the Microsoft advisory for more information.
Windows vulnerable packages
Various windows packages are not updated and these could lead to arbitary code executions in various
ways. here are the list of packages
1. Google chrome
2. .NET
3. Internet Explorer
Severity: Moderate
Remediation:
Upgrade to a version of the Unix operating system that is currently supported
Low Risk Findings
Phpinfo() Information disclosure
Applications frequently use the actual name or key of an object when generating web pages. Applications
do not always verify the user is authorized for the target object. This results in an insecure direct object
reference flaw. Testers can easily manipulate parameter values to detect such flaws and code analysis quickly
shows whether authorization is properly verified.
Severity: Low
Remediation:
Use per user or session indirect object References:. This prevents attackers from directly targeting
unauthorized resources. For example, instead of using the resource’s database key, a drop down list of six
resources authorized for the current user could use the numbers 1 to 6 to indicate which value the user selected.
The application has to map the per-user indirect reference back to the actual database key on the server.
Check access. Each use of a direct object reference from an untrusted source must include an access
control check to ensure the user is authorized for the requested object.
